Painstaking Lessons Of Info About How To Write In Cipher

The actor's technique involves writing down the first letter of every word in a vertical column.
How to write in cipher. A code is a mapping from some meaningful unit—such as a word, sentence, or phrase— into something else—usually a shorter group of symbols. 1 what is caesar cipher? How does a cipher work?
In this extract from codebreaking: There are a variety of different types of encryption. A practical guide, authors elonka dunin and klaus schmeh explain how to crack a coded message.
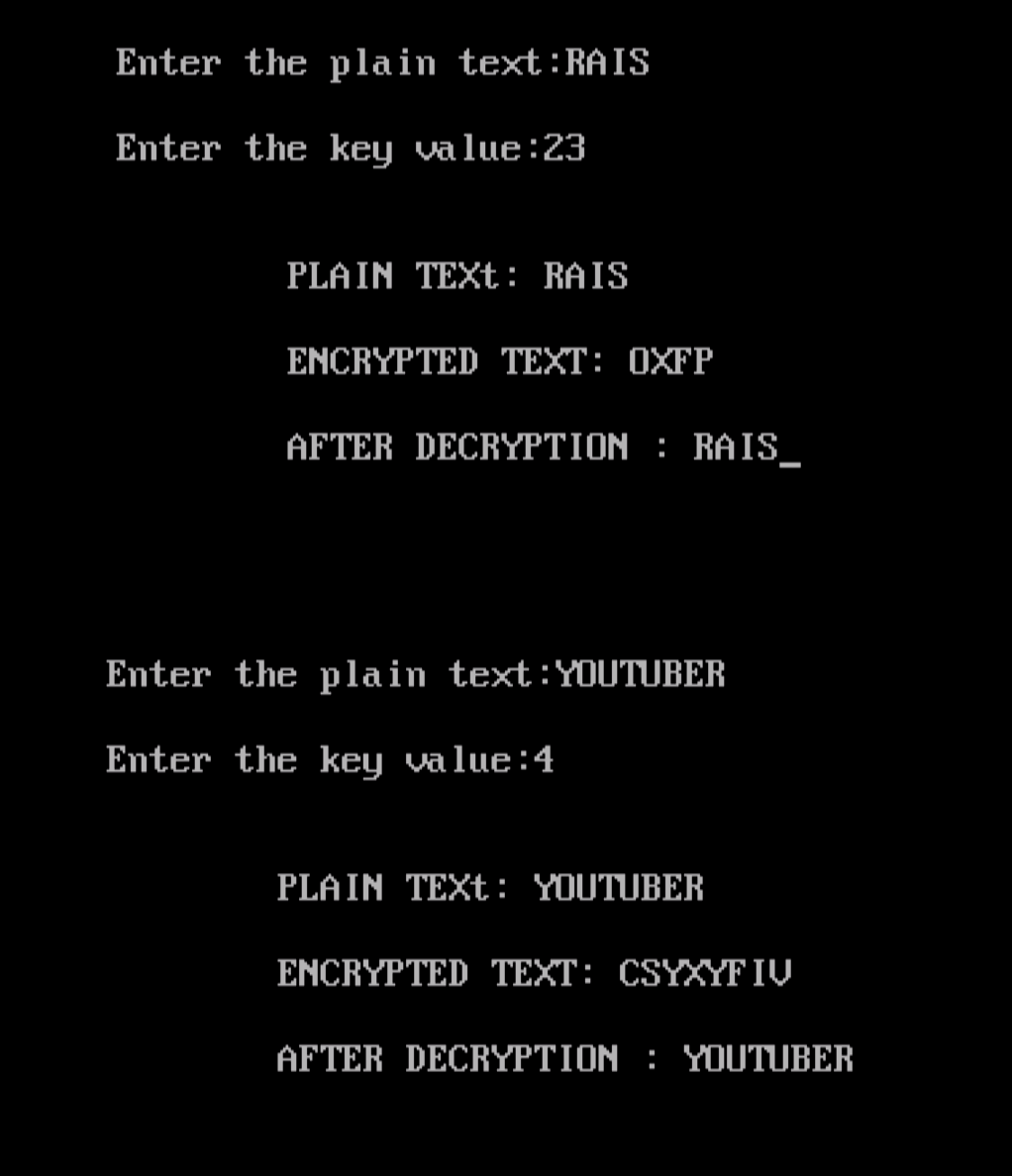
It works by shifting the. The text we will encrypt is 'defend the east wall of the castle'. To get accurate results, your ciphertext should be at least 25 characters long.
Learn about cryptography and secret codes. Convert the letter into the number that matches its order in the alphabet starting from 0, and call this number y. Find that character’s location within the alphabet.
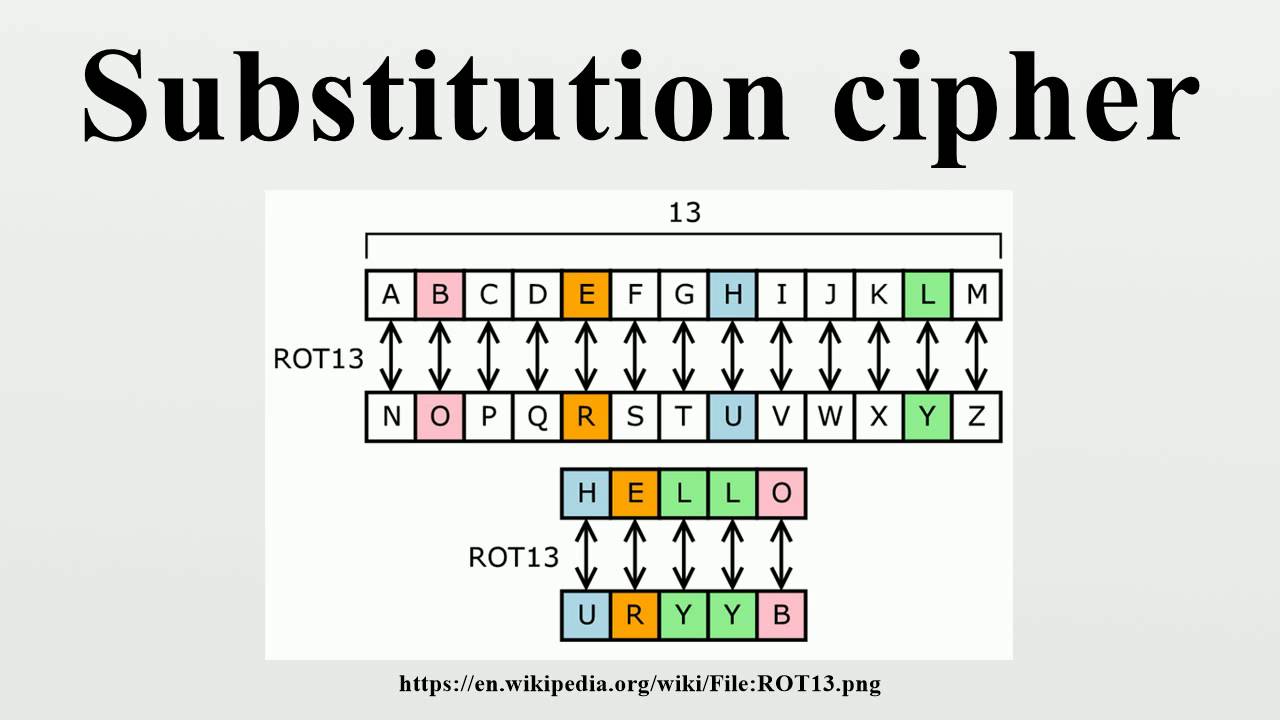
For example, we could make. The caesar cipher is a simple encryption technique that was used by julius caesar to send secret messages to his allies. Break the letter in single and add a bogus letter to the previous letter.
Algorithms used earlier in the history of cryptography are substantially different from modern methods, and modern ciphers can be classified according to how they operate and whether they use one or two keys. 3 the ord () function. The caesar cipher is one of the earliest known cryptographic systems.
The caesar cipher, also known as a shift cipher is one. Count this many letters into the alphabet. Table of contents hide.
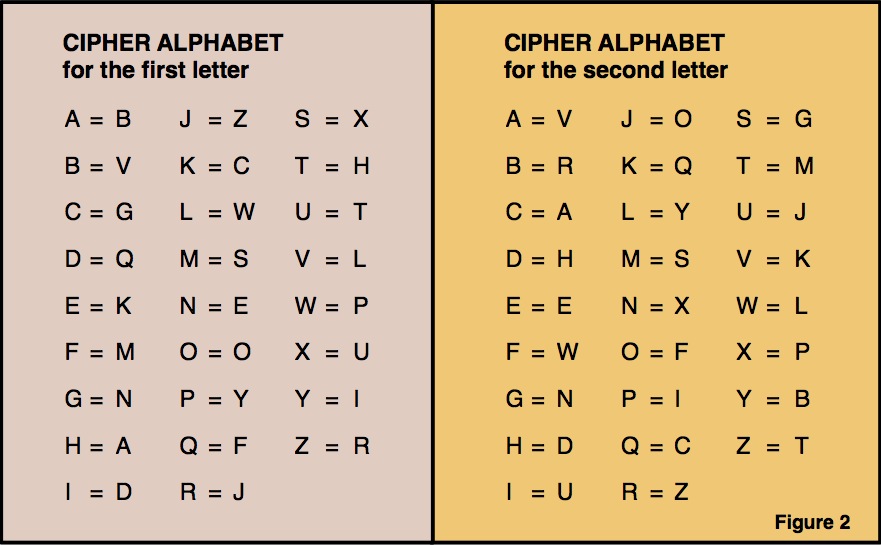
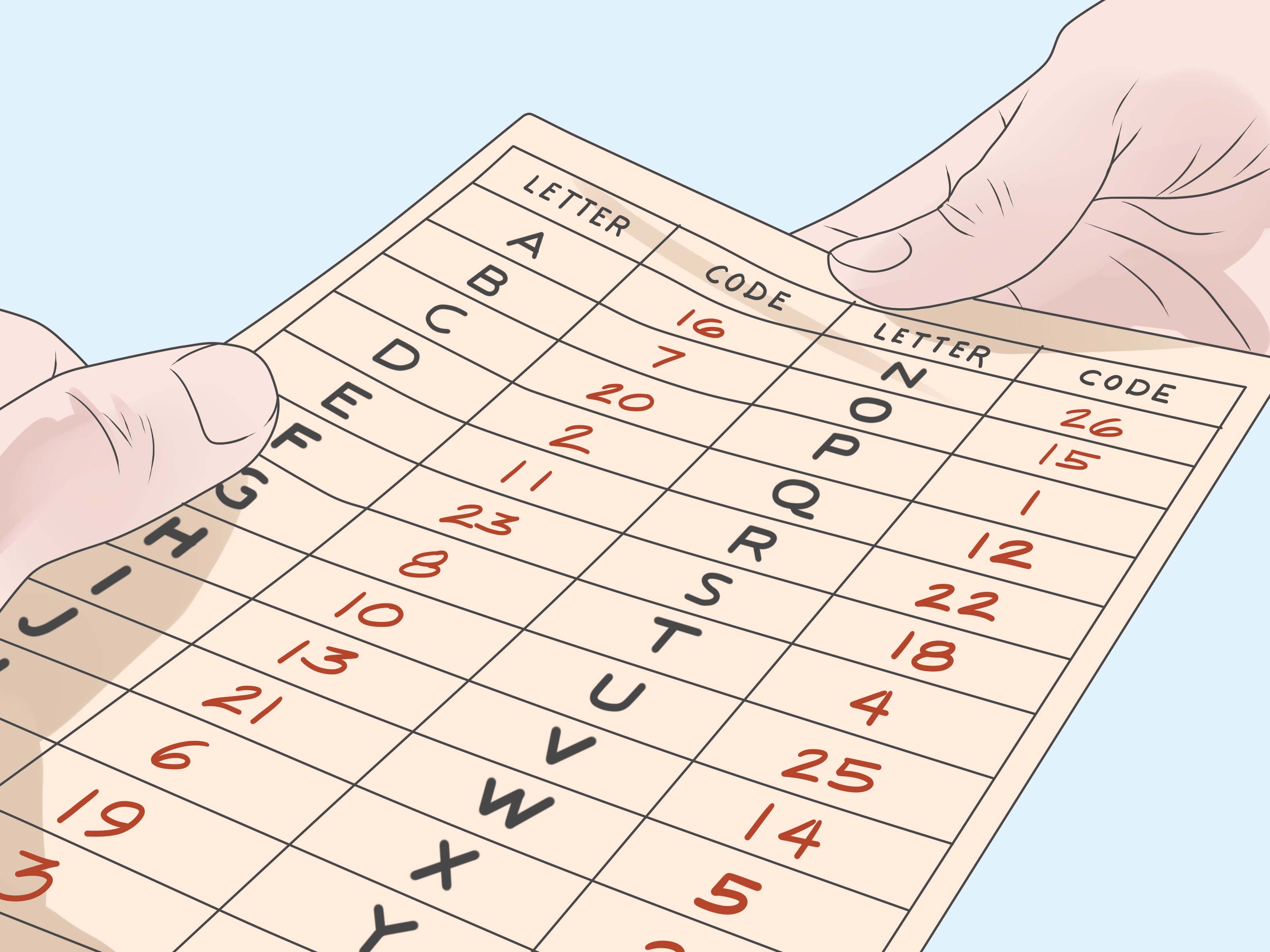
Identify the character within the sentence. When you were a kid, did you have a captain midnight decoder ring? The route cipher is a transposition cipher where the key is which route to follow when reading the ciphertext from the block created with the plaintext.
Manual decryption and parameters. Write out the entire alphabet in a line. 2 caesar cipher in python.
(a=0, b=1, c=2,., y=24, z=25) 2. 5 encryption for capital letters. Ciphers use an encryption method to change plaintext, a readable communication, into ciphertext, which appears to be a random.





![How To Write in Pigpen Cipher [2 MINUTE TUTORIAL] YouTube](https://i.ytimg.com/vi/s5XRTcLYy40/maxresdefault.jpg)